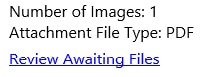
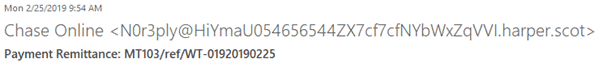I know they are fakes just by looking at them. For example, the display name of one of them says “Chase Online”, but the email address is some weird combination of letters and numbers.
In the body of the email, a link says “Review Awaiting Files”. When I roll my mouse over that, it gives a URL with a domain in the Philippines and other oddities that set my alarms off. It is obviously not a Chase email and even a cursory look shows it is bogus. I promptly deleted the email.
Phishing for Your Password
The goal of phishing is to get you to click a link and enter in your username and password. With that, the phisher can get access to emails, banking, and more, and do some real harm to you, your business, and your family.
These phishing emails are getting harder and harder to detect. They now include logos and images that look similar to what you are familiar with seeing on a secure website. Some of us are getting tricked by these and clicking the links. It must be a profitable business for the malevolent senders; otherwise, it would not be of any use to send them.
Recently someone in our company made the mistake of clicking one of these links. Oops! He entered in the username and password to his Office 365 Inbox. That resulted in the phisher sending an email to everyone in his Sent Items folder, claiming there was an overdue invoice, which was attached. Fortunately, that email looked quite suspicious and I don’t think anyone was tricked. However, we did have to field a large number of questions, which wasted everyone’s time.
And the phishers are getting even more sophisticated with their attacks. Not long ago, I received an email from LinkedIn saying I had a message from a business partner (one I knew well). I went to LinkedIn and saw that the message had a PDF attachment with a name like “RFP_NYC_PROJECT.PDF”. I downloaded the file, thinking it was legitimate, but when I went to view it, it prompted me to enter my Office 365 username and password, claiming the file was on OneDrive. At that point, I knew something was amiss – the screen looked like Office 365’s login page, with the browned out photo of Rio de Janeiro, but the domain was not something I recognized as related to Microsoft. Fortunately, my “phishing sensors” went off and I called the partner, who confirmed it was a bogus message.
After these incidents, we implemented strong anti-phishing rules on our Office 365, as well as held educational classes. While I hope we are now “phishing-proof”, we will have to stay vigilant. The phishers are using more and more tricks. The best strategy is to stay always on the defensive and be especially wary of any email that has attachments or links that require you to enter login credentials.
Implementing Office 365 Anti-Phishing Features
You can make your Office 365 safer from these attacks by implementing security features that are available in the Admin Center.
Microsoft has good documentation here about this: “Anti-phishing protection in Office 365”. https://docs.microsoft.com/en-us/office365/securitycompliance/anti-phishing-protection
One of the first things that article says is: “The most important thing you can do to secure your environment is to educate your users about the dangers and the warning signs of phishing attacks.”
This emphasizes that the first line of defense has to be “user awareness”. Be sure to hold training classes and warn users of this danger. Here is a good article from Microsoft that you can share with your users: “Protect yourself from phishing schemes and other forms of online fraud” (https://support.office.com/en-us/article/protect-yourself-from-phishing-schemes-and-other-forms-of-online-fraud-be0de46a-29cd-4c59-aaaf-136cf177d593)
Next, there are settings in the Office 365 Admin Center that you can implement. If you are on the Office 365 E5, A5, or Microsoft 365 Business subscriptions, you can implement “Advanced Threat Protection (ATP)”: https://docs.microsoft.com/en-us/office365/securitycompliance/office-365-atp. For other subscriptions, ATP comes at a monthly cost from $2 to $5 per user per month.
But even without ATP, you can set up email filtering and protection by going to the Admin Center, then Security & Compliance, then the “Threat Management” section. You can set up policies to protect against malware, phishing, spam, and bulk emails, as well as any that meet a specific criteria.
We are using these “Threat Management” capabilities in our Office 365, and it seems to work well enough. The biggest issue is that legitimate emails are sometimes blocked and we have to review the Quarantined messages (in Threat Management/Review) throughout the day to release the good ones.
Unfortunately, it is likely the phishers (and spammers and malware/virus propagators) will get more and more sophisticated. That tends to poison what is a very effective and convenient way to communicate, email. But by keeping our defenses up and users trained, as well as implementing protections available in Office 365, we should be able to keep ahead of these malefactors, at least for the most part.
I encourage every Office 365 Admin to implement policies and educate users before you suffer a phishing attack.
Meanwhile, stay aware and vigilant!
— Scott Restivo, CEO of Crow Canyon Software