Recently, we posted about how Microsoft SharePoint and Office 365 are “particularly well-suited” to managing user access requests and other critical security needs, such as security policy management and employee training. In this article, we highlight a security feature Microsoft has built in to both SharePoint Online (Office 365) and the new SharePoint 2016 release: Data Loss Prevention (DLP).
What is Data Loss Prevention (DLP)?
Office Servers and Services MVP Steve Smith gives this definition in his Microsoft MVP Award Program blog:
In a nutshell, it is a method to discover (find) and restrict sensitive data being put into SharePoint that matches specific criteria through defined industry templates and thus avoid breaches of corporate data leaving the company. Such data could include credit card details or employee national insurance or social security information and they are specific to regional requirements.
Why Data Loss Prevention in Office 365 and SharePoint 2016?
Hackers constantly seek a foothold into corporate entities, which they can use as a springboard to gain network access. Phishing techniques, social engineering, and other low-tech approaches have proven to be all too successful in gaining access to highly sensitive information, as proven by social engineering hacks against both Sony and Wal-Mart.
The exposure of sensitive corporate content is frequently initiated by an employee’s simple mistake, such as inadvertently including social security numbers or account IDs in a communication with an outside vendor. For organizations whose existence depends on maintaining regulatory compliance (e.g., HIPAA-compliant cloud service vendor), these mistakes can open the door for disciplinary actions and fines from agencies, or worse, legal actions brought against the company.
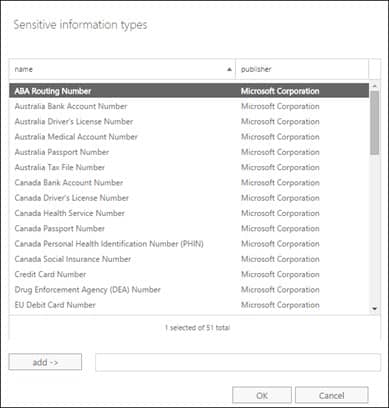
Detection and prevention of security breaches can be facilitated in an Office 365 and SharePoint environment by using the Data Loss Prevention (DLP) feature of these platforms. DLP uses SharePoint’s new sensitive information types technology to automatically monitor user activity and halt risky behavior in real-time before it can cause harm. For example, a DLP policy could monitor communications relating to customer accounts and warn about (or even prevent) transfers of information that involve credit card numbers or bank accounts. The list of available “sensitive information types” is extensive and admins can use these to fine-tune the DLP implementation to suit their organization’s security needs.
Other Information Resources
There is a growing body of information on DLP and how best to implement it. These resources below delve into the technical details of DLP and can help you understand how best to use this feature in your organization:
For DLP in SharePoint 2016, you can view our recorded webinar in our Getting Ready for SharePoint 2016 Release or check out Configure DLP in SharePoint 2016, by MVP Vlad Catrinescu
For DLP in Office 365, see refer to Technet.